Security Of Taxbandits Api Guide To Oauth Authentication
TaxBandits API has gone to the greatest lengths to safeguard our user's data from any sort of security threat. Our advanced data security architecture ensures that all our client's data are securely stored, processed, and shared through API.
Our API uses secure JSON parsers and strongly typed data to avert data intrusion. In order to clearly identify and address the errors, the status of API methods is communicated through HTTP codes.
We incorporate robust security measures and protocols that protect the data at rest as well as the data in transit.

Pre-requisites
Below are the important URLs for the Sandbox environment:
● Developer Console: sandbox.taxbandits.com
● API: testapi.taxbandits.com/version
Note : There are different API versions available such as 1.7.3, 1.7.1 and 1.7.0. You can choose the version you prefer.
● Authentication API: [https://testoauth.expressauth.net/v2/tbsauth]
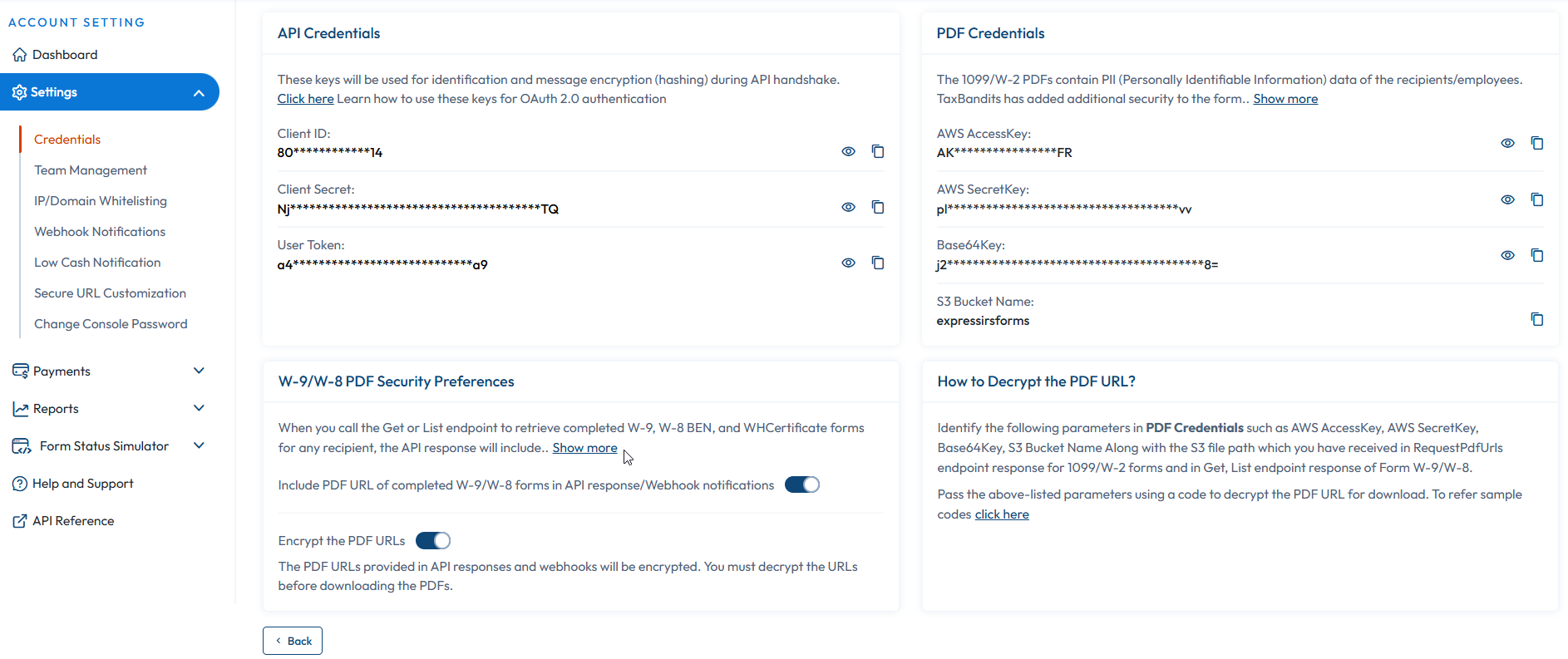
To get started with TaxBandits API,sign up for our Sandbox environment. After logging in, navigate to Settings >> API Credentials to receive the following authentication keys:
-
Client ID
-
Client secret
-
User Token
Note: Do not share the keys with any individual or business.
Security of Data at Rest
In TaxBandits API, the data at rest are subjected to end-to-end encryption. The data resides in databases, file systems, and other structured storage devices and is securely stored in MS SQL Server with the ‘Always Encrypted' feature.
Database columns containing Personal Identifiable Information (PII) such as Name, DOB, SSN, and EIN are encrypted using a symmetric key with AES 256 algorithm and stored with complete protection. The PDFs and other documents are encrypted with the AES-256 algorithm and are stored in AWS S3. Furthermore, the database connection information is also encrypted using the AES algorithm.
Security of Data when in Use
TaxBandits ensure the utmost protection of Data in transit is protected from malware attacks and other intrusions by strong network control protocols. Also, we make sure to restrict access to Secure Tunnels (TLS) and whitelisted IP addresses in the Live environment.
We don't store information if we don't have to. For example, a reference to the credit card profile is all that is maintained at our end. The actual data is stored in our merchant gateway, with very stringent security measures.
Also, all of the activities are logged and periodically reviewed. This includes IP addresses, devices, and browsers used to access the data. Also, TIN masking is done to reduce the risk of identity theft. Our support systems have Multi-Factor Authentication and IP whitelisting to prevent unauthorized access.
OAuth 2.0 Authentication
OAuth2.0 is an HTTP authentication standard, that involves a security token called Access token or JSON Web Token (JWT). Each request is authorized by validating the access token.
The access token is a cryptic string, usually generated by the server in response to a request with JSON Web Signature (JWS). The client must send this JWT in the Authorization header when making requests to protected resources.
The OAuth2.0 authentication is available on the version 1.5.0 and above in TaxBandits API.
Steps to receive Access token (JWT) by constructing a JWS
Construct a JWS according to OAuth 2.0 standards & use our tbsauth endpoint in OAuth API in the Sandbox environment [https://testoauth.expressauth.net/v2/tbsauth] to receive an access token.
https://testoauth.expressauth.net/v2/tbsauth
The JWS consists of 3 parts
-
Header
-
Payload
-
Signature
Each part of the JWS will be as illustrated below:
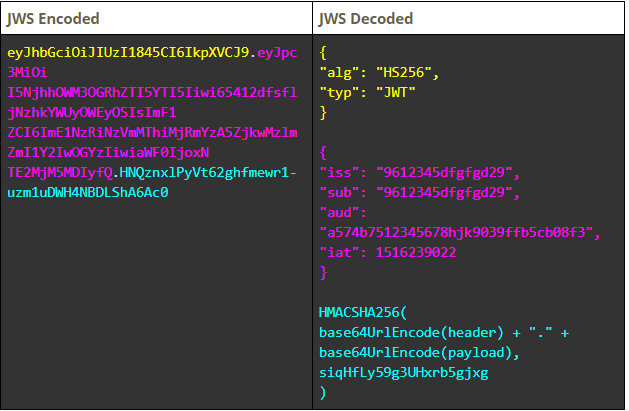
Header:
{
"alg": "HS256", /*Algorithm = HS256*/
"typ": "JWT" /*Type = JSON Web Token (JWT)*/
}
Payload:
{
"iss": "968a9c78dae29a29", /*Issuer: Client ID*/
"sub": "968a9c78dae29a29", /*Subject: Client ID*/
"aud": "a574b75f18b24fc09f9039ffb5cb08f3", /*Audience: User Token*/
"iat": 1516239022 /*Issued at: Current time (Unix epoch format)*/
}
Refer to this link for more information on the Unix Epoch standard.
Signature:
HMACSHA256(
base64UrlEncode(header) + ΓÇ£.ΓÇ¥ +
base64UrlEncode(payload),
siqHfLy59g3UHxrb5gjxg /*Client Secret retrieved from the console*/
)
Combine the header, payload, and signature concatenated with a dot (.) and applying HMACSHA256 algorithm to create the JWS.
Sample JWS:
eyJhbGciOiJIUzI1845CI6IkpXVCJ9.eyJpc3MiOi
I5NjhhOWM3OGRhZTI5YTI5Iiwi65412dfsfljNzhkYWUyOWEyOSIsImF1
ZCI6ImE1NzRiNzVmMThiMjRmYzA5ZjkwMzlmZmI1Y2IwOGYzIiwiaWF0IjoxN
TE2MjM5MDIyfQ.HNQznxlPyVt62ghfmewr1-uzm1uDWH4NBDLShA6Ac0
Below is the encoded & decoded structures of a JWS sample:
Once the JWS is created, then send a request to the OAuth server in the Sandbox environment with the JWS in Authentication HTTP header to get an Access token.
OAuth server will receive the JWS & will validate to provide the JWT (Access token) in the following response format:
{
"StatusCode":200,
"StatusName":"Ok",
"StatusMessage":"Successful API call",
"AccessToken":"eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJpc3MiOiJ0ZXN0YXBpLnRheGJhbmRpdHMuY29tIiwiYXVkIjoiYTU3NGI3NWYxOGIyNGZjMDlmOTAzOWZmYjVjYjA4ZjMiLCJpYXQiOjE1OTU5MjAxMjQsImV4cCI6MTU5NTkyNzMyNH0.BIg8764SOhOai9As3uRSidrF1-B9CxL6D5z4OggcVbs ",
"TokenType":"Bearer",
"ExpiresIn":3600,
"Errors":null
}
This JWT (Access token) will be valid for one hour. When the JWT expires, repeat constructing JWS and request the OAuth server again to receive a new access token (JWT).Note:We do not provide Refresh tokens.
Once the JWT (Access token) is obtained, its expiry can be known by decoding the JWT & reading its "exp"("ExpiresIn") claim value in the response. Remember, the same JWT must be used along with every API request until the token expires.
Requesting TaxBandits API with JWT
Every API request has to be sent along with the JWT in the Authorization HTTP header. TaxBandits Sandbox API URL is https://testapi.taxbandits.com/version
HTTP Headers required in every API request are:
Authorization: Bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJpc3
MiOiJ0ZXN0YXBpLnRheGJhbmRpdHMuY29tIiwiYXVkI
joiYTU3NGI3NWYxOGIyNGZjMDlmOTAzOWZmYjVjYjA4ZjMiLCJp
YXQiOjE1OTU5MjAxMjQsImV4cCI6MTU5NTkyNzMyNH0.BIg8764SOhOai9As
3uRSidrF1-B9CxL6D5z4OggcVbs
Content-Type:application/json
Conclusion
We frequently internal audits at regular intervals and corrects any lapses. Our Quality Assurance team consists of members who test the security (Ethical Hackers) to find potential holes in the application. Code review workshops are held periodically and secure coding guidelines are taught and reviewed.
For more guidelines & code samples on integrating with TaxBandits, check out our TaxBandits SDK, which is available in several popular programming languages.
